
Rising Magecart Attacks Place Victims in Jeopardy
Key Findings
- Magecart attacks have grown increasingly popular over the past several years. Their tactics have evolved and their ability to both breach sites and evade detection has advanced.
- Magecart has become the leading cause of Card Not Present (CNP) cybercrime in recent years. Gemini’s Magecart Overwatch system has detected 150 million payment cards compromised via Magecart attacks since 2017, which cybercriminals have attempted to monetize on the dark web for an estimated total of $37 billion USD.
- Victim organizations face steep financial, legal, and branding costs after experiencing this type of breach. This includes direct mitigation expenses, lawsuits from customers, and consumer distrust.
- Fraud teams can deploy intelligence-driven strategies to mitigate the damages of Magecart attacks. Merchants can enlist services that proactively scan their sites for any indications of Magecart infections. Early merchant breach notification dramatically lowers customer exposure, limiting both revenue loss and consumer backlash following the breach.
Background
Cybercriminals use a variety of methods to hack into targeted websites, one of the most effective of which is a Magecart attack. Magecart attacks have grown increasingly popular over the past several years. Their tactics have evolved and their ability to both breach sites and evade detection has advanced. Alongside this dangerous trend, new studies analyzing the damage inflicted to victim organizations outline the financial, legal, and branding risks that victims face.
Magecart attacks (sometimes called e-skimming) refer to injecting malicious JavaScript into a website after breaching it through leveraging vulnerabilities, employing brute-forcing attacks, phishing schemes, social engineering, or other means. These may target the websites themselves or third-party software. The breached website is then infected with an e-skimmer through one of many techniques, including direct injection of JavaScript into the HTML, injection into in-use JavaScript files, or injection of links or loaders that retrieve the e-skimmer from other files. When third-party software is granted the same access as the original company’s code, Magecart skimmers can successfully infect the domain and search for and record sensitive customer data. This often includes usernames, passwords, payment card information, and other personally identifiable information (PII). If the skimmers discretely collect enough data without detection, the cybercriminals upload their stolen data to dark web marketplaces in order to monetize compromised PII and payment records.
In-Depth Analysis
Rising Tide of Attacks
Magecart attacks have become the leading cause of Card Not Present (CNP) cybercrime in recent years. Gemini’s Magecart Overwatch system has detected 150 million payment cards compromised via Magecart attacks since 2017. Of those 150 million compromised cards, cybercriminals have attempted to monetize 124 million from dark web markets. Based on the average fraud amount per card, Gemini estimates the result of those monetization efforts to be $37 billion USD in fraud.
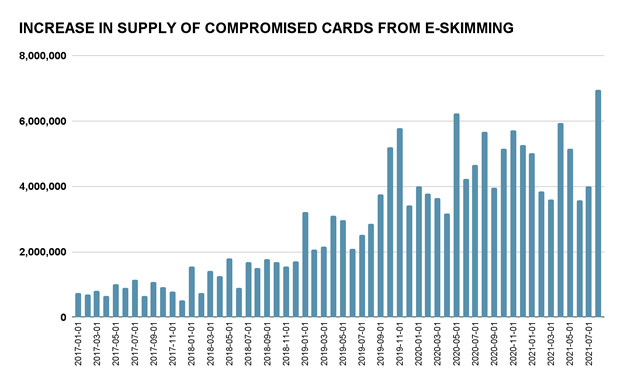
Image 1: Magecart attacks have generated an increasing supply of compromised payment cards in the last four years.
The victims of these attacks follow a familiar pattern. In the past 12 months, the United States hosted the greatest number of victim companies (nearly 5 times as many as the next largest country), followed by Germany, the United Kingdom, France, and the Netherlands. Large economies and Western nations are often the most sought-after targets, and a variety of sites using different e-commerce platforms are vulnerable to these attacks.
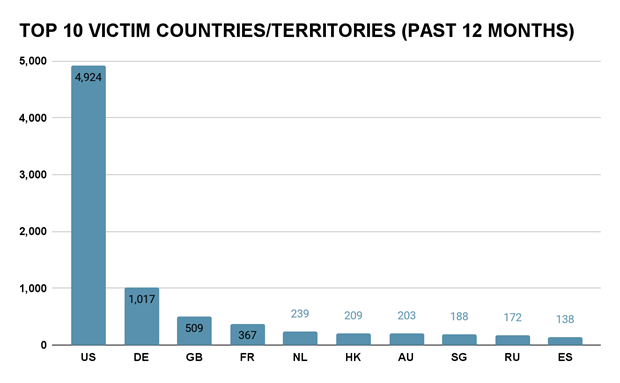
Image 2: The United States hosts the most victim websites of Magecart attacks from Gemini’s sample of more than 7,400 new infections.
While Magecart takes its name from the Magento e-commerce system, the attack vector is not just limited to Magento. Magecart Overwatch has determined that Opencart comprises 14.9% of victims, with WooCommerce at 6.2% and Shopify at 0.6%. Increasingly sophisticated tactics continually expand the pool of victims. The gap between attacker and victim technical sophistication grows even larger for organizations that use legacy versions of Magento, which account for more than 72% of Magento victims. Soft targets invite cybercriminal attention.
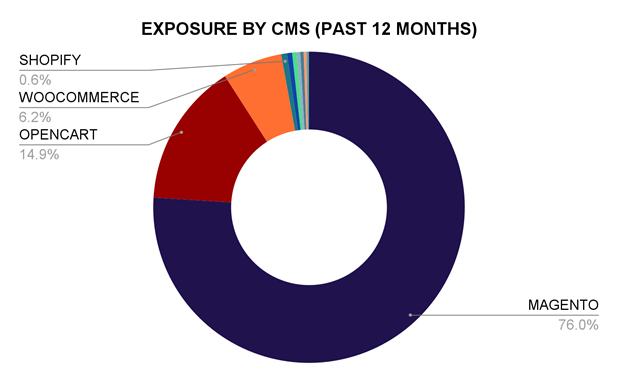
Image 3: Magento remains the most common target of Magecart attacks, but OpenCart, WooCommerce, and Shopify are still targets.
The tip of the spear for these attacks are notorious groups such as “Keeper”, which Gemini has previously covered. Their innovation, bold attacks, and demonstrated success prove to other cybercriminals that Magecart is an effective way to generate illicit income.
Impact on the Victim
As the frequency of Magecart attacks increases, the magnitude of the damages they inflict has become clear. It encompasses financial burdens, legal jeopardy, and branding crises. Since the purpose of this attack is often to steal customer payment card data, the most immediate cost is financial.
IBM’s 2021 report found that the average cost of a data breach rose from $3.86 million in 2020 to $4.24 million in 2021 (although costs were far lower for organizations with more robust security systems). This data breaks down to $1.24 million lost through detection and escalation, $0.27 million lost through notification, $1.14 million through post-breach response, and a full $1.59 through lost business cost. The most costly type of data, stolen PII, costs $180 per record; it is both the most common type of record lost and often included alongside compromised payment card data. Records overall cost $161 on average.
Scale also played an important role. The average cost of a breach with over 50 million records exposed was $401 million, a $9 million increase from last year and almost 100 times more expensive than breaches of 1,000 to 100,000 records. IBM additionally found massive disparities between those organizations that deployed AI, automation, hybrid cloud environments, or had high levels of regulatory compliance and those that did not, with costs significantly lower for the more proactive and compliant organizations.
Breached companies also need to contend with the legal fallout from a data breach. Consumers whose data was exposed during the hack often seek damages, financial restitution, transparency about the breach, among other demands. Some high-profile lawsuits resulting from data breaches include AMCA (which declared bankruptcy shortly afterward), Click2Gov (more than $5 million in controversy), Hanna Andersson (which settled for $400,000), and Wawa (judge granted preliminary approval for $12 million settlement).
An organization’s brand can suffer as well. A May 2021 study by PYMNTs and NuData indicated that 65% of e-commerce shoppers “are likely to terminate their relationships with merchants after experiencing even a single instance of data theft or payment fraud.” Even if a company survives the immediate financial fallout and the legal ramifications, customers may lose interest in transacting with an organization known for inadequate data protection. Failure to invest in or react swiftly to Magecart attacks carries a heavy price.
Modern Tactics
Magecart attacks have evolved to include more subtle infiltration methods that make it more difficult for security researchers, and especially ordinary consumer sites, to detect a hacker’s malicious script. Several such methods include:
- Co-opting Google Tag Manager to host malicious scripts
- Exfiltrating stolen data to Telegram
- Hiding scripts within Scalable Vector Graphics (SVG) elements
- Employing steganography.
Recently, Magecart actors have added a new tool to their bag to circumvent the use of third-party payment platforms such as PayPal Express Checkout. They have begun to use scripts that inject a fake payment card data collection form into the checkout process. For sites that use a step-based checkout system, the actors typically insert the fake form into the billing information step. Most sites just collect the payee name and billing address in this step, but it does not seem out of place for payment card information to be collected here as well, making it an ideal insertion point for the fake form. Sites using the step-based system typically have a final step which is where the customer is forwarded to the third-party platform to complete payment. Sites using a single page layout, where billing, shipping, and payment collection forms are visible at the same time are also being victimized via fake forms. In these situations, the malicious actors overlay the third-party payment section with the fake form and once the data is entered and the form submitted, the checkout process redirects to the third-party system.
Fraud teams can deploy intelligence-driven strategies to mitigate the damages of Magecart attacks. With prompt detection, financial institutions can identify at-risk payment cards and monitor their portfolios in real time, allowing them to reduce fraud mitigation turnaround to 24 hours. This allows them to proactively identify compromised points of purchase (CPPs) before they even receive chargeback data.
Mitigation
It’s not only banks or card issuers that can take proactive steps to reduce Magecart attacks. Merchants can enlist services (such as Magecart Overwatch) that proactively scan their sites for any indications of Magecart infections. Early merchant breach detection dramatically lowers customer exposure, limiting both revenue loss and consumer backlash following the breach.
Conclusion
Magecart attacks are a dangerous attack vector with demonstrated success against a variety of e-commerce targets. They have increased in volume, sophistication, and impact, and have grown popular among cybercriminals capitalizing on the rising demand for compromised CNP records among dark web fraudster communities. Their victims suffer from financial, legal, and branding consequences, driving the necessity for a more robust security strategy. Because the timeline between a Magecart breach and the fraudulent transactions on stolen cards is relatively short, a proactive approach is the most practical way to stay ahead of these attacks.
| Tagged with: |
| Posted in: | Uncategorized |
